|
|
|
# Carna Botnet
|
|
|
|
|
|
|
|
The Carna Botnet was created by anonymous security researchers to measure the extent of the internet. Checking the activity of a large number of IPV4 addresses would be impossible for a single system. In order create the internet census of 2012, the researcher would need a botnet.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
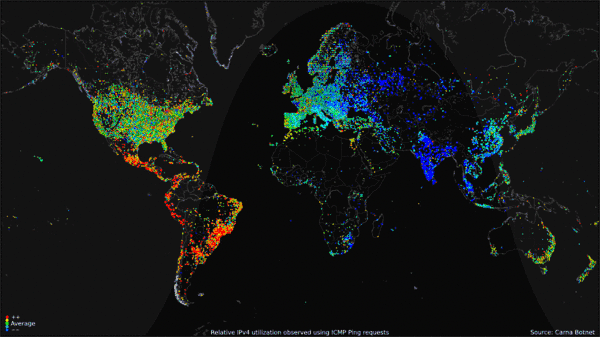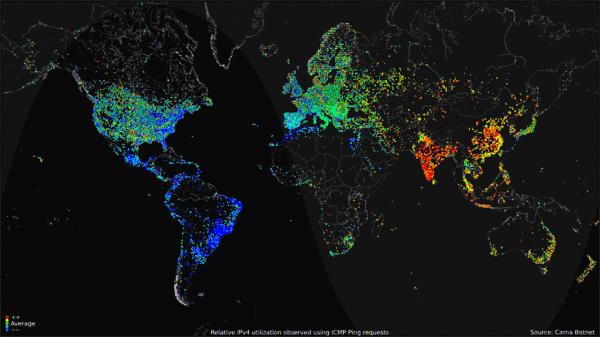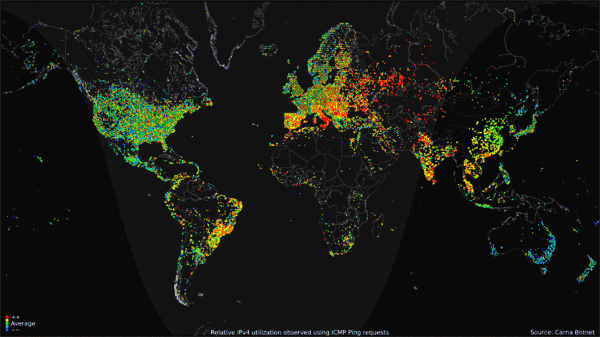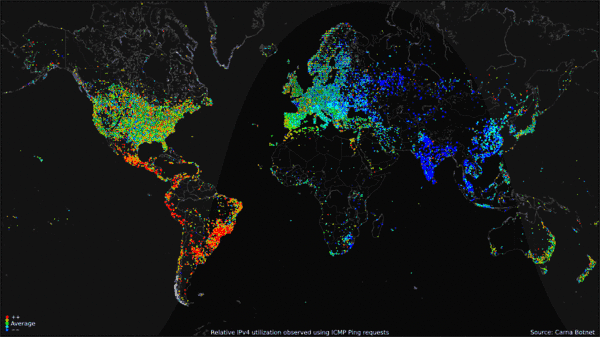
The Internet Census of 2012 ran from June to August. This gif shows the average utilization of IPV4 devices over a 24 hour period.
|
|
|
|
|
|
|
|
## Exploit
|
|
|
|
The exploit was simple, the first computer would infect devices with default usernames and passwords, through a total of four username/ password combinations. Infected devices would access exploit other devices through the same exploit. The architecture of this botnet is extemley unique, with no need for C&C, since all devices are available directly. The researchers reported:
|
|
|
|
- 420 Million IPs responded to ICMP ping requests more than once.
|
|
|
|
- 165 Million IPs had one or more of the top 150 ports open. 36 Million of these IPs did not respond to ICMP ping.
|
|
|
|
- 1051 Million IPs had a reverse DNS record. [Map] 729 Million of these IPs had nothing more and did not respond to any probe.
|
|
|
|
|
|
|
|
A lot of users keep default passwords on their devices. These are extremely easy to exploit, and even create a botnet with as shown through the Carna Botnet.
|
|
|
|
|
|
|
|
## Ethics
|
|
|
|
Although the reasearchers could have done many malicous things with the new botnet, they claim "We had no interest to interfere with default device operation so we did not change passwords and did not make any permanent changes". They published their findings openly, yet their data is sometimes ignored due to the unethical method of obtaining it.
|
|
|
|
|
|
|
|
##### source:
|
|
|
|
http://census2012.sourceforge.net/paper.html
|
|
|
|
[Carna Botnet](/Vulnerabilities) |
|
|
|
\ No newline at end of file |